According to the news, 23andme has settled for $30 million dollars but does so with statement not admitting any wrongdoing.
Which I agree with. I’ll tell you why. I don’t think anyone should receive a dollar from this unless you were a family member of someone who was breached.
Why?
In October 2023, 23andMe revealed that unauthorized access to customer profiles occurred through compromised accounts. Hackers exploited credentials stolen from other breaches to access 23andMe accounts.
Quite simply, I don’t believe 23andme has a duty of care to download all databreaches and compare passwords.
It was the users fault for using the same password across multiple services. That’s why it is called a credential stuffing attack.
If you use the same password on every website, and one of those websites get hacked, the hacker now has access to all of your services.
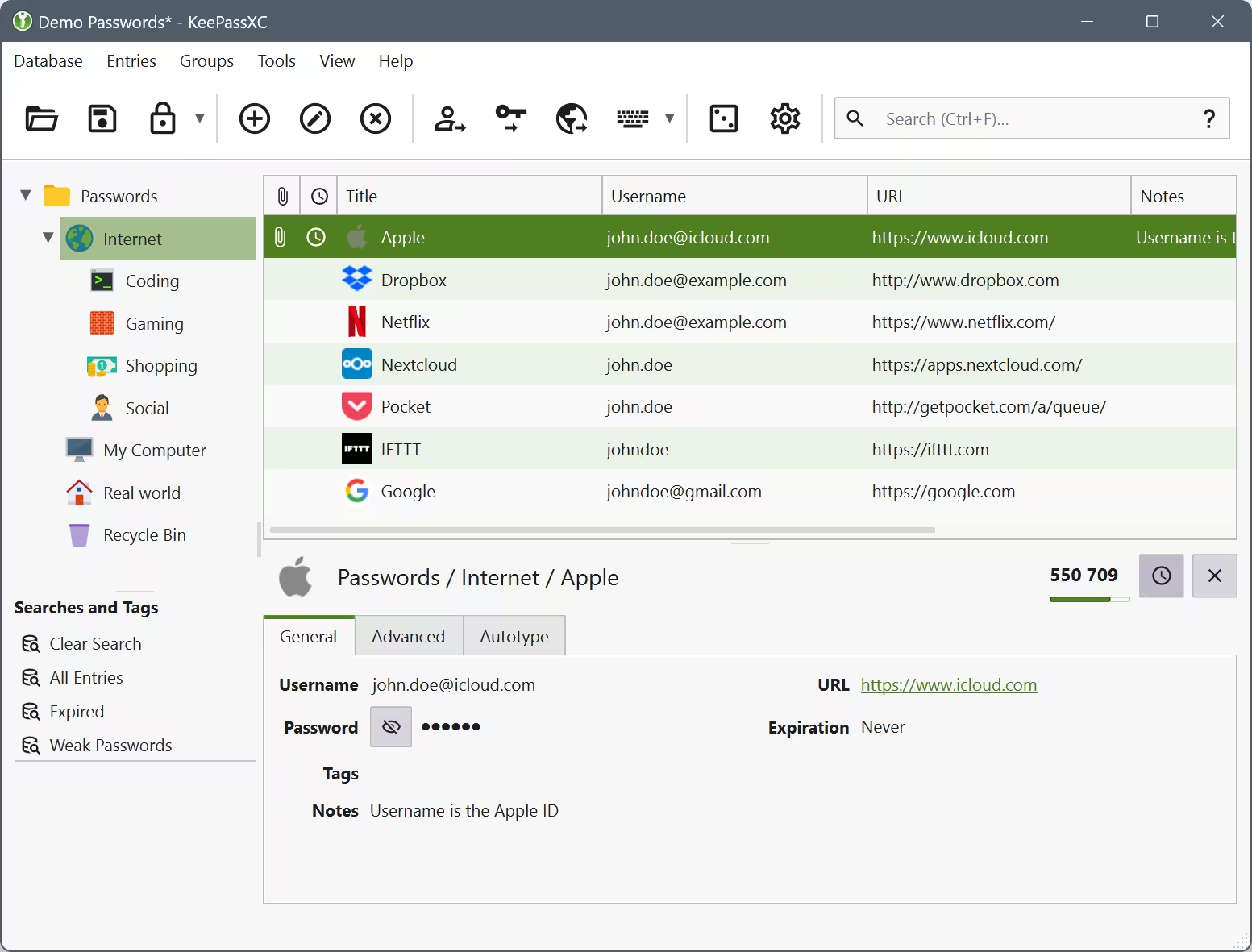
That’s why you should use something like KeePassXC to help you keep track of and generate random passwords for each and every service.
KeePassXC is an amazing tool. It can generate passwords and there is a browser plugin and ssh agent. You remember one password to unlock KeePassXC and then you can either copy pasta or use the browser plugin.
Why is it 23andme’s fault?
Sure, they could detect when a user’s ip address accesses multiple accounts. That’s why I’m not arguing against the settlement. They had some part of the blame, but I would still put most of the blame on the user.
IP addresses are tricky. What do you do when you have a bunch of users using the same VPN exit? It’s not so clear.
Or multiple people with 23andme accounts sharing the same wifi.
Or people who use Tor.
It’s not as easy as you might think and enforcing 2fa was a great thing to do for their users to prevent future breaches.
Who else forces 2fa? Practically nobody. Even Google makes you turn it on.
And downloading data breaches can be legally dubious at best because of data controller concerns with all the extraneous data they do not need to hold onto to detect breached passwords. These breaches contain more than just passwords most of the time.
Can your company reasonably download a dump that may contain credit card info? addresses? personal info of non customers?
Imagine the liability of that when non customers find out you’re holding their data.
Conclusion
I think that users should be educated, that using a password manager should be common practice and I don’t think 23andme violated their duty of care.